Mission Control Plugins

Executive Summary
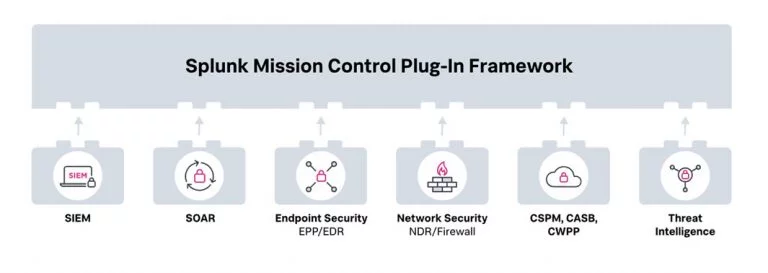
Splunk Mission Control’s Plug-in Framework offers
capabilities to build Plugins, which provide instant contextual, enrichment, and threat intel info correlated with the incidents for an analyst to quickly triage the incident, it also has dedicated features to search for relevant incident’s events and get the pinpoint insight required during a security investigation, these results into significantly reducing a SOC’s MTTA & MTTR.
Crest Data developed a number of closed and open-source Mission Control Plugins using the plugin framework for a number of customers across CASB, Threat Intel, EDR, VAPT, and Cloud solutions
Business Challenge
One of the top challenges of a SOC is the “cry wolf effect” or understanding the incident before triage and escalation. It’s not only the multitude of alerts but the fact that many of these alerts are false positives that create stress and reduce the effectiveness of analysts’ responses. One survey found that more than half of the respondents reported a rate of 50% or higher of false-positive alerts, leading to spending the majority of SOC’s time trying to analyze the high volume of alerts. So instead of chasing wild geese, SOC needs a way to reduce the time required to determine if an alert is true or false.
Even after an alert has been deemed important enough to investigate further, analysts need threat intelligence (TI) to enrich the associated data and assess the full scope of the breach, additionally, they also need all the relevant information such as network log files, endpoint logs, etc. All of this needs to be done quickly to prevent your environment from catastrophe. Today, this process involves switching across tools, context & manually traversing through voluminous log files which makes it time-consuming and cumbersome.
Customer Solution
Splunk Mission Control’s Plug-in Framework offers capabilities to build Plugins, which provide instant contextual, enrichment, and threat intel info correlated with the incidents for an analyst to quickly triage the incident, it also has dedicated features to search for relevant incident’s events and get the pinpoint insight required during a security investigation, these results into significantly reducing a SOC’s MTTA & MTTR.
Crest Data developed a number of closed and open-source Mission Control Plugins using the plugin framework for a number of customers across CASB, Threat Intel, EDR, VAPT, and Cloud solutions
The Crest Difference
Crest Data, being strategic partners of Splunk helped them develop plugins for early access partners since its beta program, groom & harden platform capabilities, and delivered intuitive Customer demos.
Jainil Desai
Technical Project Manager @ Crest Data











