Public Cloud Shared Responsibility Model: Things to Know

A shared responsibility model
is a cloud security structure that governs the security oversight of a cloud infrastructure and its components and dictates accountability to the vendor or customer and its users.
The responsibility of securing an organization’s IT infrastructure when it is on premise within its own data center is clear, you own the entire stack. The company is responsible for maintaining the operation and health of the applications and data hosted on the internal servers.
But as companies move to Public Cloud Solutions, the security model changes and defining who is accountable for which component of the infrastructure can be complicated. Where does the vendor’s security responsibility stop and where does the customer’s obligations begin?
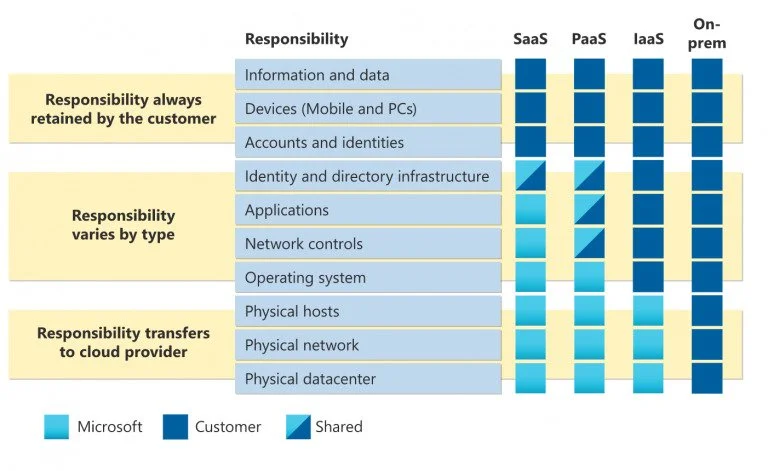
Responsibilities Divided
As you navigate the landscape of public cloud security, one challenging thing you’ll realize is that each vendor can have different shared responsibility models. The type of cloud service deployment whether it be, (IaaS) infrastructure as a service, (PaaS) platform as a service, (FaaS) function as a service, or (SaaS) software as a service can define different security obligations and assignments for vendors and customers.
As a starting point, the following diagram from Microsoft illustrates the areas of responsibility between the customer (you) and the vendor (in this case Microsoft),
Regardless of the type of deployment, the following responsibilities are always retained by you (the customer):
Data
Endpoints
Account
Access management
Source: Microsoft
Keep in mind that in most cases Cloud Service Providers (CSP) will not cover all of the cloud security responsibilities, it is important to confirm this with your CSP. The customer responsibility will depend on the cloud services the customer chooses and which applications installed and configurations made. Most CSPs are responsible for the security of the cloud infrastructure and the customer is responsible for the security in the cloud and the applications running on it.
Challenges
While this model is a framework designed to define ownership of your cloud environment. It also brings a set of challenges for the end customer.
Understanding Shared Responsibilities – The security workload responsibilities of the CSP vs. the customer are sometimes not clearly defined. These gray areas often come up leaving an organization confused about security ownership.
The first step to mitigating issues of ownership is to have clarity of the security responsibilities. Understand the literature and gather the documentation of the CSP’s shared responsibility model so your team can make informed decisions to address any gaps and vulnerabilities.
Skill Gap – The skill gap that exists in the industry leads to organizations being unprepared to address the complex shared responsibility model in the cloud.
A global annual study from Systems Security Association (ISSA) and industry analyst firm Enterprise Strategy Group ESG, states that the cybersecurity skills crisis continues… and has impacted more than half (57%) of organizations, the top ramifications of the skills shortage include an increasing workload for the cybersecurity team (62%), unfilled open job requisitions (38%), and high burnout among staff (38%). Further, 95% of respondents state the cybersecurity skills shortage and its associated impacts have not improved over the past few years and 44% say it has only gotten worse.
Addressing the skill gap in the security space is not easy but have your team members who are security-aware to be your biggest advocates and leverage their skill sets here. If your team doesn’t have the technical expertise to address the security concerns of your environment, you may look to MSPs that can provide a comprehensive cloud security solution.
Shadow IT – This refers to the use of devices, software, applications, IT systems, technologies and services without corporate IT approval. Employees may decide to adopt certain software or services because they find them to be more efficient for their workflow or more comfortable and familiar to use.
With WFH being ubiquitous during COVID-19 and many using tools from cloud vendors to perform daily tasks, shadow IT has increased significantly as employees have introduced software and tools that have been unchecked and not explicitly vetted and approved by the IT department. This can present cybersecurity vulnerabilities and can lead to data breaches. Companies may not have a proper incident response plan for such threats.
Some examples of shadow IT are file-sharing services, project management tools, email services, and messaging apps. With so many cloud services available and easy to set up with only an email and a few clicks, using these technologies unchecked poses security and compliance risks for organizations.
Most cloud vendors will have a version of the shared responsibility model. And the security and compliance consequences and impact introduced in the cloud environment may still be under the ownership of your organization.
In many cases, employees are only trying to increase productivity but may not fully understand the security vulnerabilities and implications it could cause. Unsanctioned software and even hardware to store sensitive company data with a personal email account can easily be used to exfiltrate data to outside parties and leave it susceptible to security leaks and data compromise.
Having an elevated security culture and visibility over your organization’s cloud environment will help to mitigate shadow IT. Adopting AI and ML monitoring security tools will also help to proactively detect threats and anomalous activity.
Next Steps
As an organization, teams need to have full clarity on the security responsibilities of the company cloud environment. Understand and communicate this to all stakeholders to align on individual, team, and organizational accountability and ownership to avoid any security gaps.
Companies may also opt for an end to end cloud security solution from a security vendor that offers a cohesive view on the infrastructure and delivers a comprehensive managed security package.
Crest Data has worked with Fortune 500 companies as well as some of the world’s most innovative companies and hottest startups to streamline work processes so teams can perform at their highest level.
Contact us to learn more about our Product Engineering solutions and our broad range of managed and professional services that encompass solution implementation, building integrations, enable migration, and health checks, and see how we can help you today.
Author
Tuan Nguyen
Tuan is a Product Marketing Manager with 8+ years of industry experience in large Enterprise technology companies and start-up. He is passionate about technology marketing and has experience in Cybersecurity, Cloud Security, and Data Center Networking.